Bossie Awards 2017: The best networking and security software
InfoWorld picks the top open source software for protecting networks and their users

The best open source networking and security software
We seem to be witnessing a renaissance in open source security. Security projects swarmed the Bossies last year, and the hits kept coming in 2017. Along with the many cool tools for security pros, our winners include software that tracks vulnerabilities in the open source libraries used to build software. Open source, heal thyself!
[ InfoWorld presents the Best of Open Source Software Awards 2017: The best open source software development tools. | The best open source machine learning tools. | The best open source cloud computing software. | The best open source databases and analytics software. ]

Signal
Encrypted messaging apps are all the rage, and Signal continues to hold its own in an increasingly crowded space. WhatsApp, Google Allo, and Facebook Messenger all use the Signal protocol to handle the encrypted chats. Why not use the real thing and skip the middleman? Signal offers end-to-end encryption by default, a feature that must be manually enabled for Facebook Messenger and Google Allo. In 2017 Signal added video chat and revamped how safety numbers are handled. Signal also got high scores in a security audit at the end of last year, yet another vote of confidence for the app.
—Fahmida Rashid

Privacy Badger
Aggressive browser tracking is a big problem, and the Electronic Frontier Foundation’s Privacy Badger—an extension for the Chrome, Firefox, and Opera browsers—helps Internet users fight back. Privacy Badger 2.0 introduced support for incognito/private browsing and the ability to import and export settings to other browsers. The new release also fixed past privacy issues, such as WebRTC leaking IP addresses and HTML5 <a ping> tracking. More a privacy tool than an ad blocker, Privacy Badger helps Internet users block stealthy online tracking while unlocking content from sites that comply with the EFF’s Do Not Track policy.
—Fahmida Rashid
Aardvark
The principle of least privilege—giving users the most basic permissions they need and nothing more—is hard to manage, especially in sprawling cloud environments. Netflix engineers came up with Aardvark to retrieve all of the data gathered by Amazon Web Services’ Access Advisor service about which AWS services IAM roles have access to, and when those services were last accessed. For a two-punch knockout, combine Aardvark with Repokid, another Netflix-developed tool, to determine which permissions the role doesn’t need and remove them.
—Fahmida Rashid

Phinn
Phinn is a Chrome extension that uses machine learning to detect phishing websites. Phinn is pre-trained for AWS, Dropbox, GitHub, Google Accounts, Microsoft Office 365, Outlook.com, Salesforce, and Twitter, but can be trained for other services used by your organization. Phinn takes screen captures of log-in pages and passes them to the pre-trained neural network to distinguish fraudulent forms from the real thing. It also conducts checks against the web serving domain to determine its authenticity.
— Victor R. Garza

IsThisLegit
IsThisLegit is a tool for gathering and responding to reports of phishing emails within an organization. A Chrome extension allows end users to simply click a button in Gmail to report suspected phishing attempts. These alerts are rolled into a dashboard that allows security analysts to organize and view the incidents, determine the authenticity of the reported emails, and respond to the users. The project is currently working on clients for Outlook and Outlook 365. IsThisLegit comes from Duo, the company also behind Phinn.
— Victor R. Garza

Securitybot
Security analysts are in a constant race against the sheer number of alerts. Securitybot, developed by Dropbox, reduces the number of alerts by using a Slack chatbot to automatically reach out to the employee to confirm whether the user performed the actions (many failed log-in attempts, log-in attempts from unknown devices, or attempts to access restricted fileshares, for example) that triggered a security event. If the employee says no, Securitybot alerts the analyst to the unauthorized action.
—Fahmida Rashid
VersionEye
VersionEye monitors Git repositories and sends notifications when it finds public vulnerabilities, license issues, and outdated versions of third-party components. Recently, the project added “inventory diff,” the ability to look at two versions of a project’s open source inventory list and see all the changes in the project’s dependencies. This is quite handy if the project is using a newer version of Java and you need to know what dependencies were added and what was removed from that version.
—Fahmida Rashid

Security Graph Language
The open source security experts at SourceClear understand that software applications are vulnerable to security flaws lurking in third-party libraries and components. Security Graph Language, or SGL, is a query language researchers can use to identify security issues in open source code. SourceClear made the language specification and reference architecture available as open source. A dedicated environment in which researchers can write queries and hunt for issues is on the way.
—Fahmida Rashid

StrutsHoneypot
Vulnerabilities in open source frameworks are particularly problematic because they impact all applications that rely on that framework. Cymmetria released the StrutsHoneypot earlier this year to help detect and block exploits targeting specific vulnerabilities in Apache Struts. An Apache 2 mod, the honeypot can be launched via Docker. Cymmetria has other task-specific honeypots in its arsenal, such as MTPot for detecting whether a device is part of the Mirai botnet.
—Fahmida Rashid
Bitscout
Developed by Kaspersky Lab researcher Vitaly Kamluk, Bitscout lets forensic investigators remotely analyze a compromised system and collect necessary artifacts such as malware samples. Bitscout can trace and detect malware in a system without making any changes to the system. The remote investigator gets root privileges inside a virtual container, and uses the text-based user interface to install additional software, securely transfer complex pieces of data to the lab, scan other systems with custom Yara rules, and make changes to the system from the container, just to name a few potential tasks.
—Fahmida Rashid

Rudra
Developed by the security experts at Qualys, Rudra lets security analysts analyze files and classify them as bad or good. Visual Structural Analysis (VSA) highlights structural patterns within files and can be used to cluster unknown/untagged binaries into families. Rudra isn’t intended to replace existing static analyzers or dynamic behavioral analysis. Analysts can use heuristics along with Rudra output to classify a file as a new member of a known malware family, or as a member of a new one.
—Fahmida Rashid

XRay
XRay is an open source intelligence (OSINT) gathering tool for penetration testers and security professionals. Used to automate network mapping and reconnaissance, XRay relies on the Shodan search engine and DNS queries to gather information from public networks. For every unique IP address and open port, XRay will launch specific banner grabbers and collectors to get OSINT information.
—Fahmida Rashid
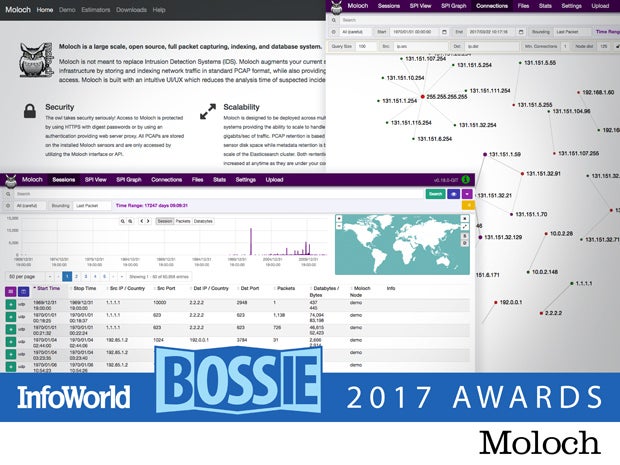
Moloch
Similar to Wireshark, but focused on network security, Moloch displays full packet capture information in a simple web interface. Unlike other tools, Moloch is designed for large-scale use, drawing on its own database and indexing system based on Elasticsearch. Moloch can ingest PCAP network packet capture files and search extremely large datasets to assist investigations. While tools like Wireshark have more filtering and display options, Moloch displays more security relevant data, and in a more focused manner, making it more useful for the security investigator.
— Victor R. Garza

Ncrack
Ncrack is a command-line tool designed for high-speed, large-scale auditing of credentials over the network. It uses a syntax similar to John the Ripper and Nmap, runs on Windows, Linux, MacOS, and BSD Unixes, and supports numerous network protocols including FTP and Telnet, HTTP and HTTPS, MySQL, PostgreSQL, Windows RDP, SMB, SSH, and VNC. Ncrack can perform brute force guessing attacks against a single service, a group of hosts, or a range of IP addresses, giving you a list of found credentials. It is a strong motivation to get those weak passwords fixed.
— Victor R. Garza

LEDE
A “reboot” of the OpenWrt router firmware project, LEDE like Openwrt supports a wide range of devices and target architectures and simplifies configuration and upgrades with a convenient web-based UI. Unlike OpenWrt, LEDE has committed to a steady and transparent development cycle. The LEDE development team merges patches faster, updates dependencies more frequently, and relies on more recent Linux kernels and toolchains. Case in point: The most recent LEDE release uses kernel 4.4.71, whereas the previous OpenWrt release used 3.18.
— Serdar Yegulalp
Copyright © 2017 IDG Communications, Inc.
















