The best open source software for cloud computing
InfoWorld’s 2018 Best of Open Source Software Award winners in cloud computing

The best open source software for cloud computing
The question used to be, “What container orchestration platform are you using?” Now the question is, “So, how are you running Kubernetes?” The past year has seen Kubernetes continue its domination, with managed “K8s” clusters being offered by all three major cloud providers, and lots of innovation happening in the surrounding ecosystem. Our 2018 Bossie winners in cloud computing are ushering in the new era of cloud-native applications.
[ InfoWorld presents the Best of Open Source Software Awards 2018: The best open source software for software development. | The best open source software for cloud computing. | The best open source software for data storage and analytics. | The best open source software for machine learning. ]
Kubernetes
There was a time when other options were considered for container orchestration. But when it comes to running distributed containerized applications today, Kubernetes has consolidated its dominance. If you’re going to deploy a new scalable service across AWS, Azure, GCP, or your private cloud, Kubernetes is likely going to enter the conversation.
Building any container infrastructure means supporting a whole ecosystem of hardware, software, and network devices. With the Kubernetes 1.11 release, Kubernetes now supports IPVS in-cluster load balancing and CoreDNS (a pluggable DNS server). This follows major security, storage, and networking enhancements earlier in the year.
— Andrew C. Oliver
Docker
Docker allows you to package your software in “containers” and run them as an OS-level virtual machine. As opposed to VMware and other popular virtualization technologies, Docker doesn’t waste CPU or other resources virtualizing a whole computer, or require an additional OS for each “guest.” In just five short years Docker has totally changed the way virtualization works in computing.
With the ascension of Kubernetes, Docker is no longer the way most people are looking to distribute containers. However, Docker is certainly still a viable alternative for managing container clusters, and it continues to be the way most people create and run individual containers.
— Andrew C. Oliver
Istio
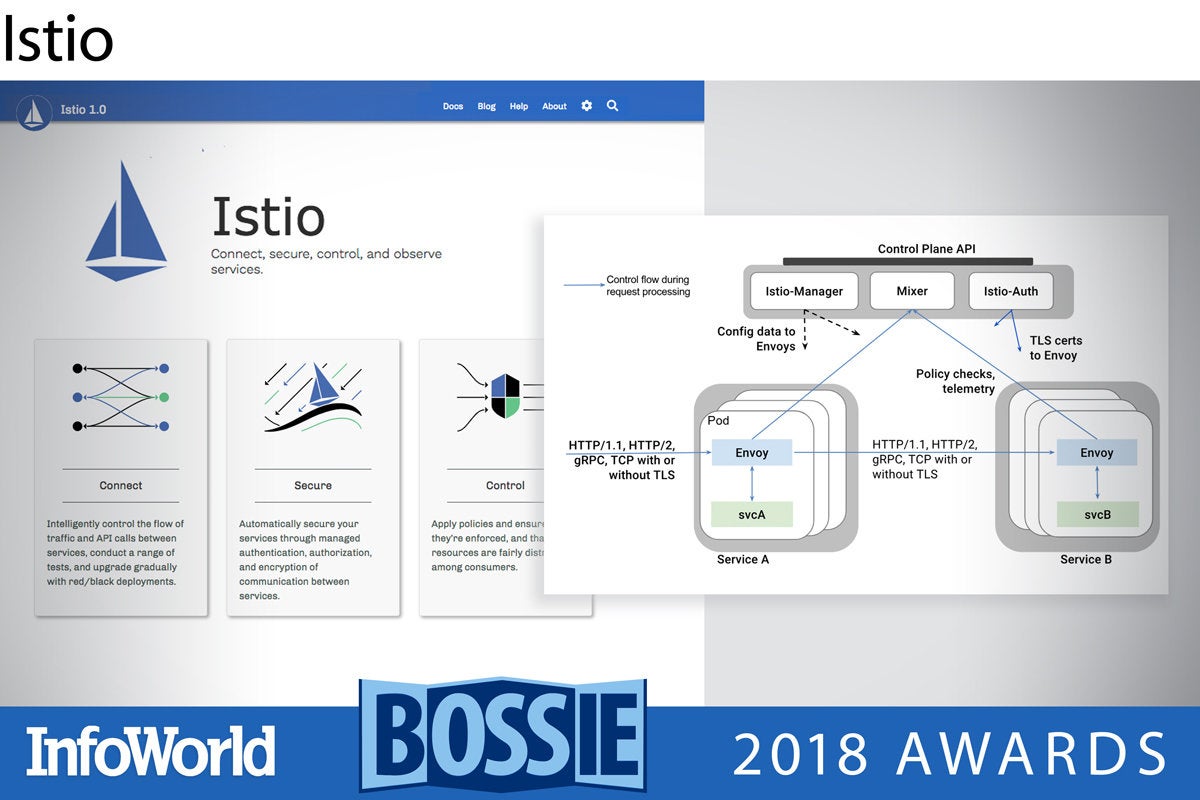
Istio is proving to be an important part of the container deployment puzzle. Sure, platforms like Nomad and Kubernetes provide many capabilities for container orchestration, but they tend to provide the bare basics for defining services rather than addressing the more esoteric needs around and between the various services in your enterprise.
Istio provides a service mesh on top of your orchestration platform, allowing you to define relationships and handle richer operational requirements like discovery, load balancing, failure recovery, metrics, and monitoring. Released by Google in 2017 and reaching 1.0 earlier this year, Istio is handling massive production deployments on Google Kubernetes Engine, and it is likely to become an important part of the wider Kubernetes ecosystem.
— Ian Pointer

Envoy
Created by Lyft, Envoy is so good that even arch-rival Uber uses it. By including features like service discovery, health checking, load balancing, and an out-of-process design architecture that makes it easy to use with any type of application server, Envoy has rapidly become a key part of the Kubernetes ecosystem, allowing some of the complexities of cluster networking to be abstracted away for developers.
You’ll find Envoy at the heart of Istio’s service mesh system, as well as being separately deployed in Kubernetes clusters all over the world. Envoy also serves as a shining example of how modern C++ applications can still show newer, more fashionable languages a thing or two.
— Ian Pointer
Apache Zipkin
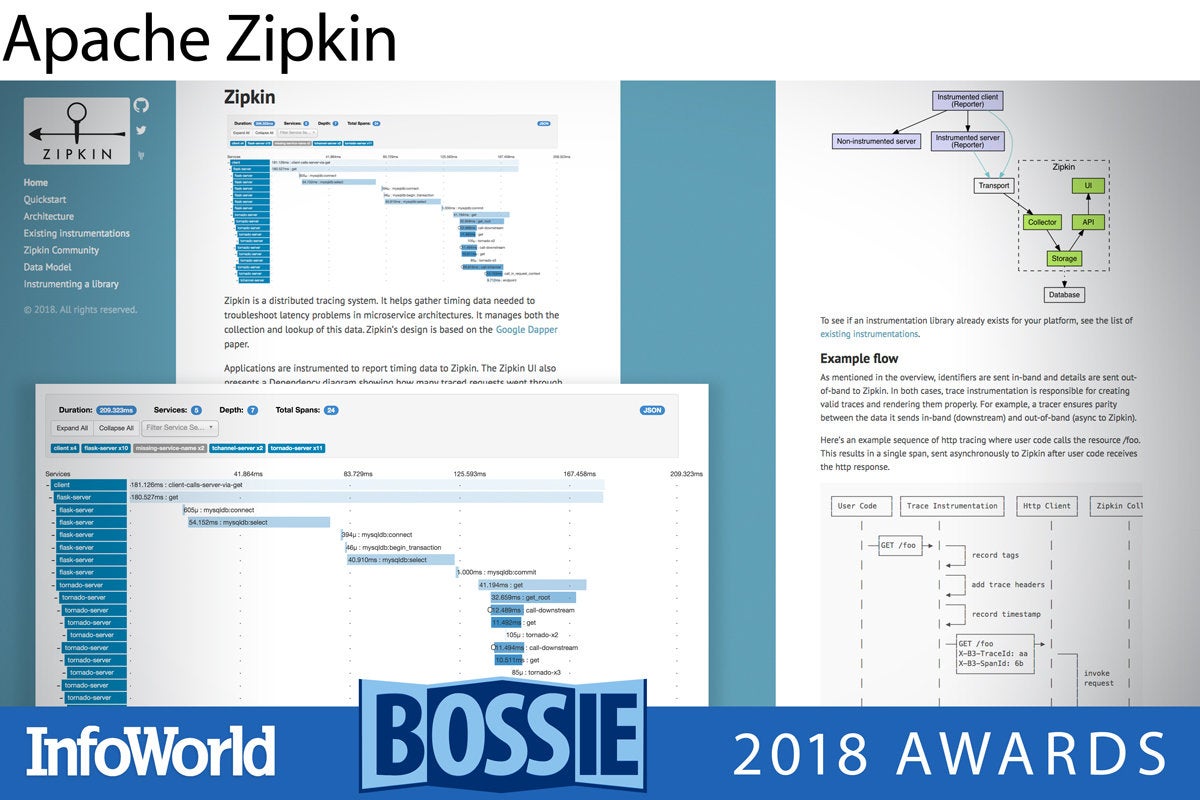
Today’s increasingly distributed and microservice-oriented architectures offer many advantages in terms of scaling, resiliency, and developer productivity. But there is a big drawback in terms of debugging: With so many moving parts and potentially different locations, it can be difficult to pinpoint exactly where an issue is occurring.
Originally developed by Twitter, based on concepts described in Google’s Dapper paper, Zipkin is a tracing system that maps the requests travelling through your architecture, allowing you to identify latencies and potential issues in your system. Already a popular choice for distributed debugging, Zipkin’s recent adoption as an Apache Incubator project should see it become even more widespread as we go into 2019.
— Ian Pointer
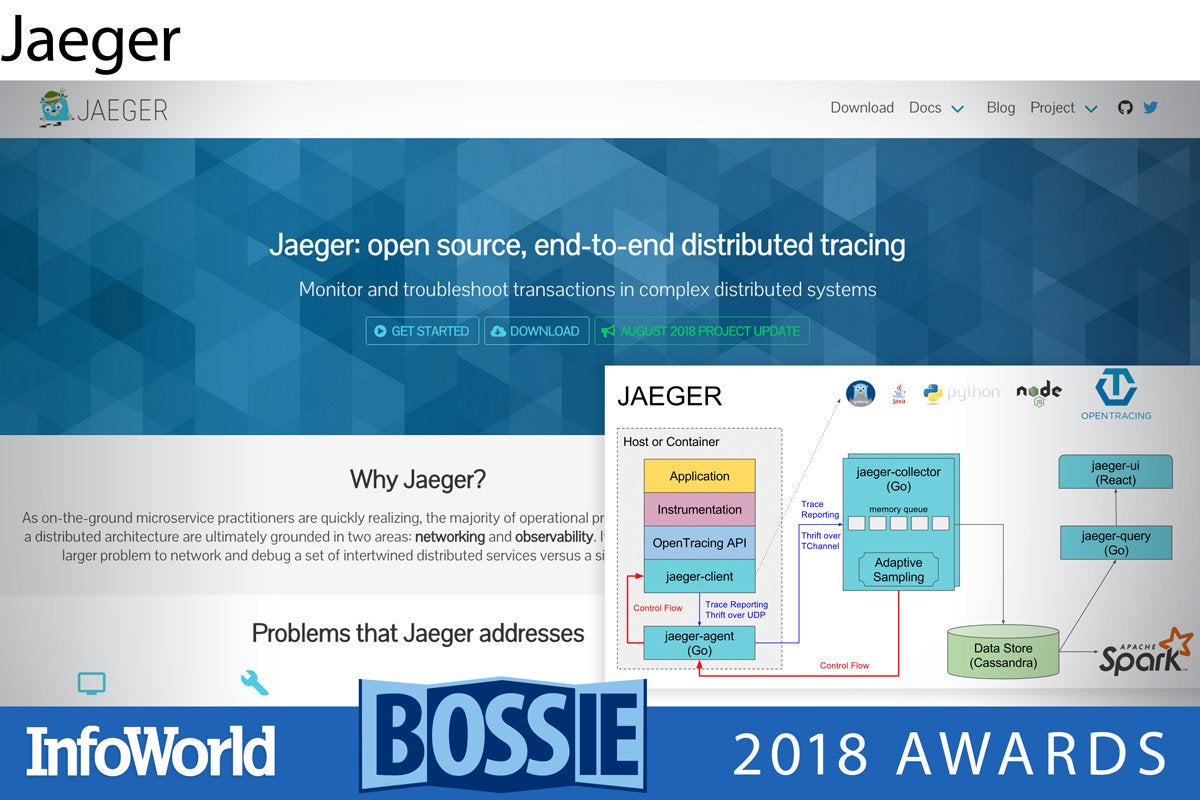
Jaeger
Jaeger is a distributed tracing system for Kubernetes. Uber readily embraced microservices some time ago. However, there is something to be said for a monolith. You can keep a log somewhere and know exactly what your monolith was doing and when. When you break the application into pieces and distribute it all over the network, you get a lot of benefits in terms of scalability and adaptability, but you also have no idea what is doing what, when, and where. If part of the network goes wonky, how do you know where the errors began? For Uber the answer was to develop a tool that lets you write, collect, and analyze “traces”—metadata used to track requests across processes and services—which hopefully tell you what did what where and when so that you can find the root cause of your latency.
— Andrew C. Oliver
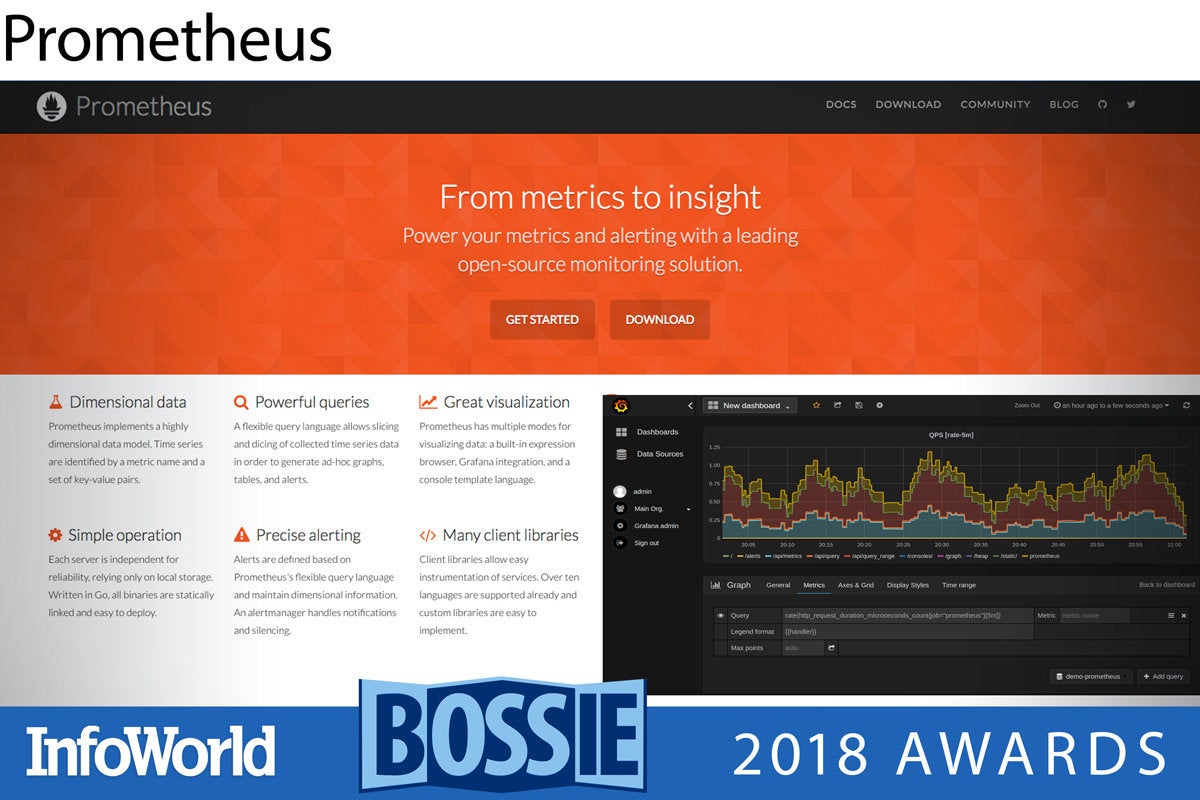
Prometheus
A Cloud Native Computing Foundation project alongside Kubernetes and Istio, Prometheus was likewise built for working with distributed applications in the cloud. Prometheus provides monitoring and alerting services, backed by a homegrown time-series database designed to handle high-velocity data ingestion.
Instrument your code with Prometheus’s client libraries—available for Go, Java, Scala, Ruby, and many other languages—and you can collect time-series data via pull or push. Plus, Prometheus works with other CNCF projects as a component, meaning it can use the Kubernetes service discovery features, for instance, but doesn’t have to.
— Serdar Yegulalp

Kops
toward the companion tools and techniques that fill in the gaps. Example: Kops, an all-in-one command-line tool that automates the provisioning of Kubernetes clusters in AWS, Google Cloud, and VMware vSphere, with other target platforms either in progress or planned. Kops can also generate Terraform configurations, allowing you to use Hashicorp’s infrastructure manager to deploy Kubernetes clusters. And Kops supports migrations from the earlier Kube-up tool too.
— Serdar Yegulalp
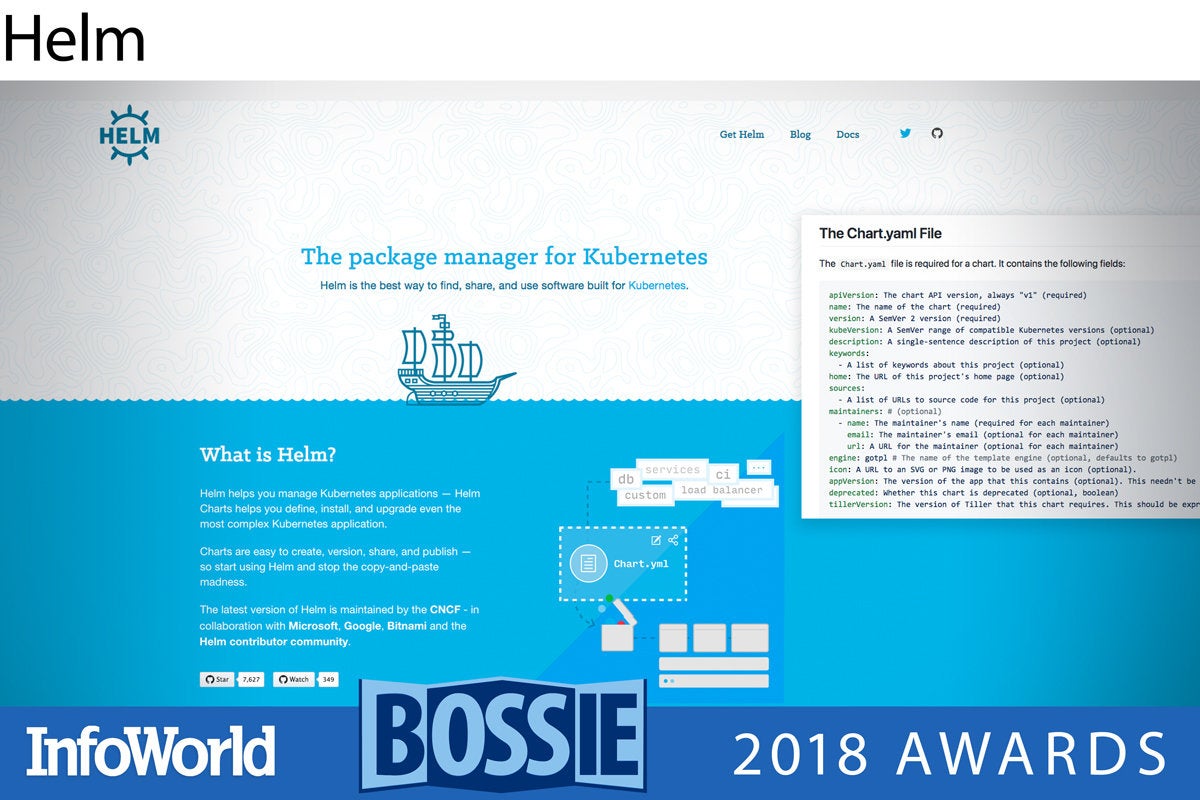
Helm
Helm is an application installer for Kubernetes. After you’ve developed a few containerized applications and deployed them throughout a Kubernetes cluster, the shine starts to wear off quickly. There is a ton of configuration (i.e. network, storage, limits) that lives outside of your container lifecycle. Keeping with the nautical theme, Helm lets you package all of this in “Helm charts.” Essentially Helm is the package manager and charts are the packages—but instead of packaging just your container, charts include the “other stuff” around your container.
— Andrew C. Oliver
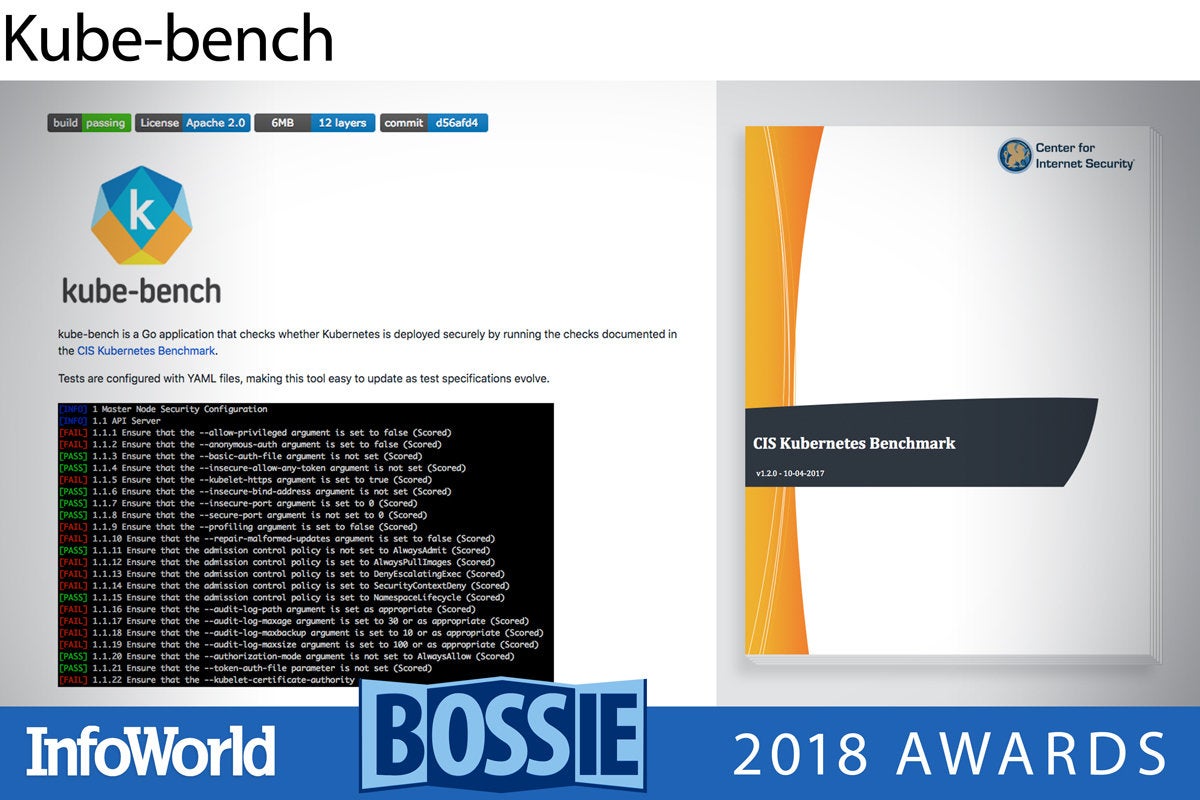
Kube-bench
Kube-bench is a Go application that tests the security of your Kubernetes deployment against an industry standard benchmark, the CIS Kubernetes Benchmark from the Center for Internet Security. Sparing you countless hours of manual drudgery, Kube-bench creates an extensive set of automated checks from the 275-page guide to Kubernetes best practices and security recommendations.
As Kube-bench runs through its tests, the tool outputs Pass, Fail, or Warning messages with the corresponding section of the CIS Kubernetes Benchmark for lookup. Kube-bench also supports JSON output for reiterative automation, integration with other tools, and subsequent remediation of security issues. Tests are configured in YAML format, making it easy to update them as the CIS benchmark evolves.
— Victor R. Garza
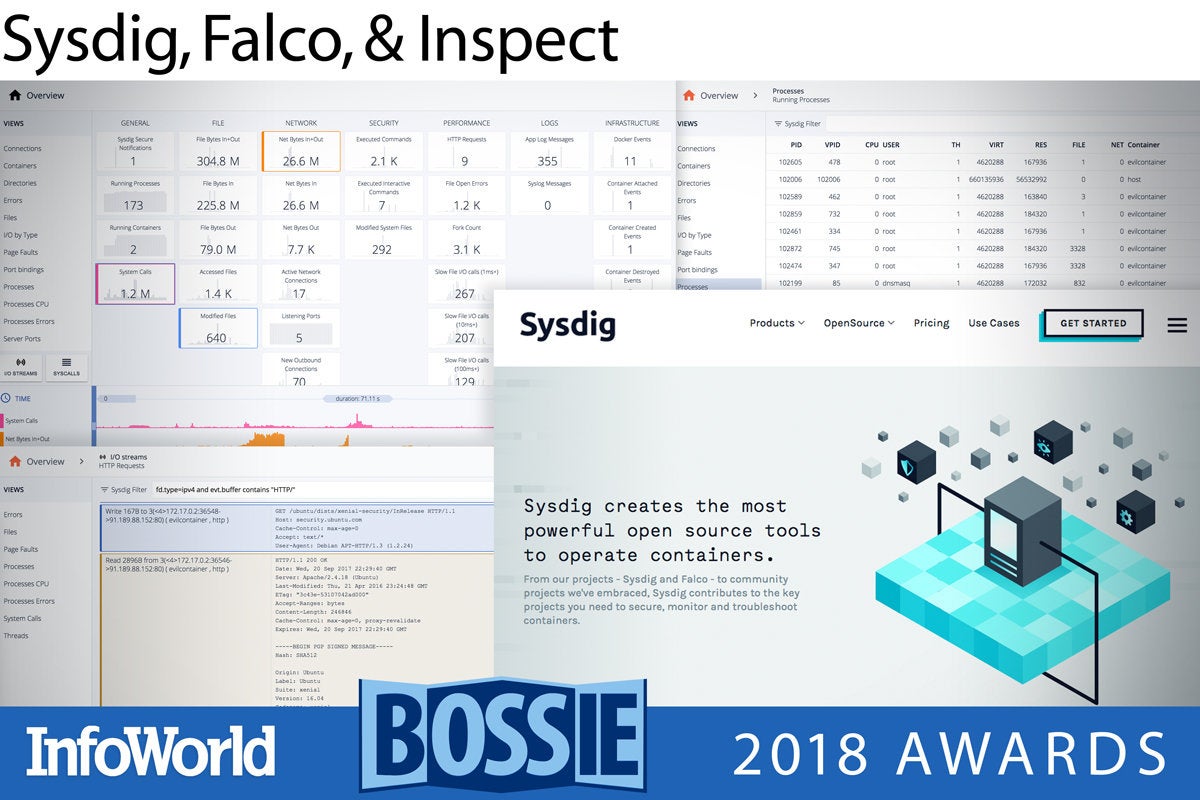
Sysdig, Falco, & Inspect
Behavioral monitoring and anomaly detection have worked well for enterprise networks for decades. Now Sysdig is bringing them to your container platforms. Drawing on the popular Sysdig system call capturing tool and your own custom rules expressed in Sysdig’s event filtering language, Sysdig Falco detects security policy violations and anomalous behaviors in your Linux containers and container hosts.
After discovering a violation with Falco, you can use Sysdig Inspect to do a deep-dive forensic investigation into the system, network, and application data you’ve captured with Sysdig. Along with visualizations of system calls and performance metrics, Inspect lets you drill down into details on processes, file system activity, network connections, and payloads. Every byte of data written to files is on display to assist in malware detection and incident response investigations.
— Victor R. Garza

OpenFaaS
The serverless approach is appealing for many reasons. Sure, there’s the cost savings related to on-demand infrastructure. Even better, the paradigm feels like a maintainable way of creating and deploying Anything-as-a-Service. For the benefits of the pay-per-use model, you suffer vendor lock-in. But what if you didn’t have to make that choice?
Enter OpenFaaS, a serverless model that deploys functions as Docker containers on a Kubernetes cluster. Deploy that Kubernetes cluster anywhere and you never have to worry about vendor lock-in. You might not get the same financial benefits unless your Kubernetes cluster auto-scales, but you gain deployment flexibility while getting to use your new favorite programming paradigm.
— Jonathan Freeman
Serverless Framework
Serverless architecture has been taking over the world for a few years now, but the approach typically requires significant vendor lock-in. Each cloud provider that offers to execute functions or “lambdas” has specific details about implementation and deployment that make it difficult to migrate to other cloud providers.
If you use the Serverless Framework, however, you abstract some of those differences away while gaining convenient ways to test and deploy your functions. You interact with Serverless Framework through a CLI, which helps bootstrap and deploy serverless functions to various cloud providers and allows configuration updates via a common YAML file. At three parts convenience, one part lock-in prevention, the Serverless Framework is worth a strong look.
— Jonathan Freeman
Copyright © 2018 IDG Communications, Inc.














